
Security System
Barista applications can take full advantage of the framework's role-based security system. Each user must be assigned to at least one role. Within each role, access can be set for applications, individual tasks, and even individual fields. The security system also contains an auditing mechanism to log changes to desired files, which can help meet compliance guidelines. Security for a given application is typically mapped out and implemented by the system administrator; the following overview provides application users with a general understanding of the system.
Users, Roles, Permissions
For convenience, users can either be created in Barista and then exported to Enterprise Manager, or existing Enterprise Manager users can be imported into Barista. At a minimum, the User Name, Firm ID, Document Group, and Language ID must be defined for each user. Leave the Expiration Date blank if the user account should never expire.
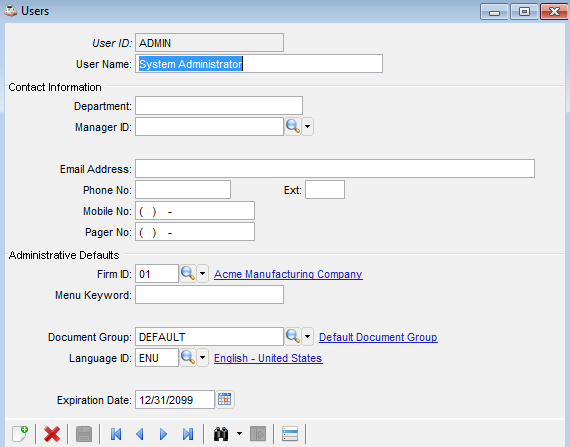
Barista Administration > Security > Users
Setting up a role definition is simple, requiring only the Security Role ID and Security Role Description, and optional Effective/Expiration Dates. Checking the Administrator box means there are no restrictions for the role.
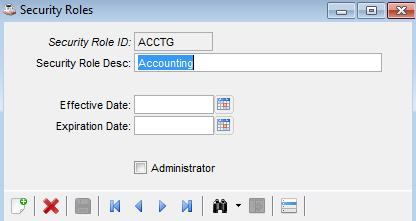
Barista Administration > Security > Security Roles
Once users and roles are defined, one or more roles are assigned to each user by accessing the User Security Roles item on the Additional Options menu for the Users form. When a user is assigned more than one role, the permissions from all roles are aggregated when determining the user's access to a particular form, field, or process. In short, this means that if access to a particular task/field is allowed in any of the user's roles, then access will be granted unless any one of the roles denies access.
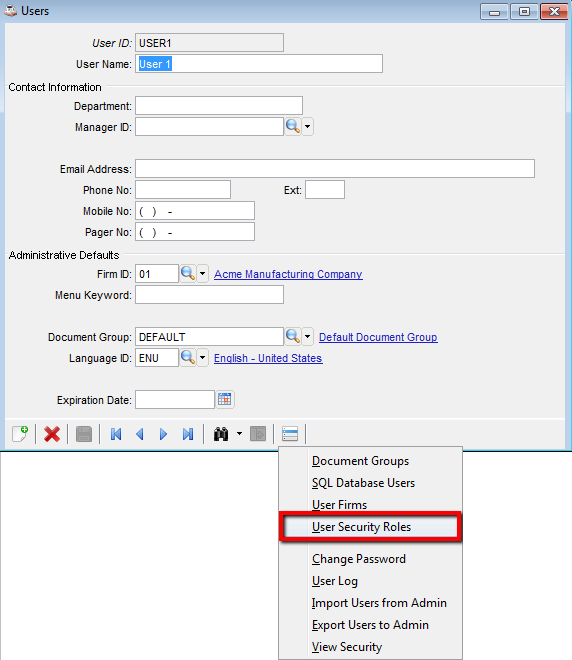
Set User Security Roles
It is also helpful at times to see which users have been assigned to a given role. Access that information from the Additional Options menu on the Security Roles form.
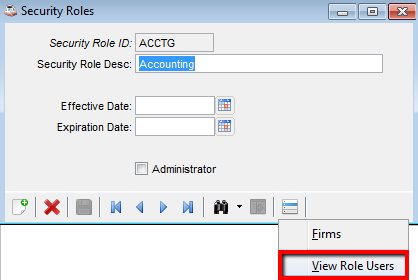
View Security Role Users
Security Levels
Simply defining a role tells the application nothing about the permissions for that role. The Security Administration form is the place to establish permissions for the applications, tasks/forms, individual fields, and selected processes, as well as settings for auditing. This point and click form uses a series of icons to show how permissions change from allowed to denied to unspecified each time the user clicks the mouse or presses the spacebar.
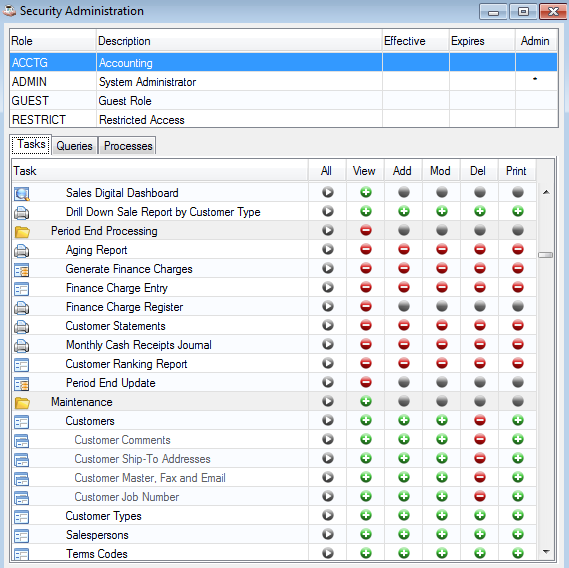
Security Administration shows access to Period End Processing menu is disabled and the delete permissions for the Customer Master and subform records
Double-click in the Security Administration grid on a row such as Customers to access and/or set field level security and auditing for that form.
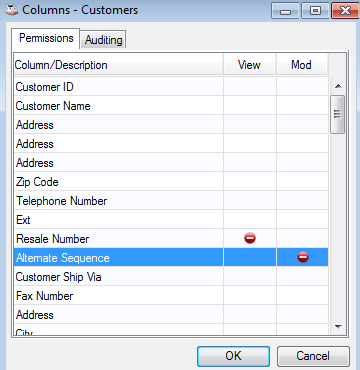
Field level security for the Customers form; cannot view the Resale Number or modify the Alternate Sequence
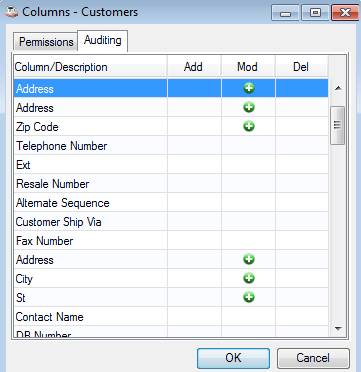
Auditing turned on for the address fields in the Customer form
If security settings are high level, disabling entire menus or tasks/forms, then users simply won't see those menus or items on the menus. In the case of field-level security, controls for which view or modify permissions are denied will display on the form, but the contents will be either hidden or set to read only.
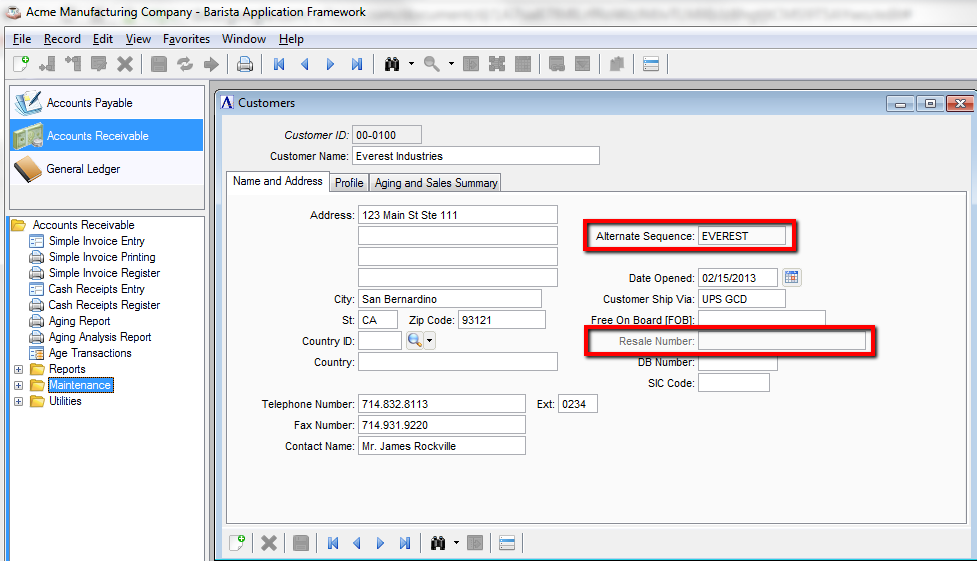
User logged in with limited access to applications and tasks. Alternate Sequence cannot be modified, and Resale Number cannot be viewed
NOTE: Not all tasks are run from the applications menu. Some tasks are launched from the Additional Options menu on a form. If a user selects an option from the Additional Options menu and doesn't have adequate security clearance, Barista displays a warning.
Access is restricted warning
Auditing
When auditing is enabled, Barista tracks all requested additions, changes, and/or deletions in its Audit Logs. The logs track when a change was made, who made the change, in what form/task, in which field, and what the before/after values were.
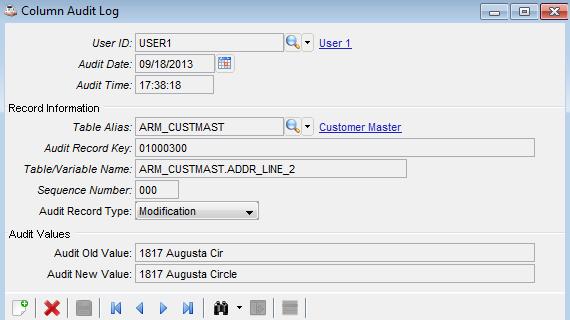
Audit log capturing a change in the address for company 01, customer 000300
Queries and other Processes
Barista security also provides administrators with a way to set permissions on fields displayed in custom queries, and on other assorted processes, such as whether users can access the Processing Settings form, or are allowed to manually adjust column widths in reports.
______________________________________________________________________________________
Copyright BASIS International Ltd. BARISTA®, AddonSoftware®, BBj®, Visual PRO/5®, PRO/5®, and BBx® are registered trademarks.