
Enterprise Manager - Web- SSL Configuration
Description
In BBj 17.0 and higher, multiple SSL ports can be configured for the integrated Jetty Web Server. This requires multiple keystores and Enterprise Manager allows the administrator to configure the SSL keystore(s).
To access the SSL Configuration, go to Web and double-click SSL Configuration in the BBj EM Navigator. The Settings tab opens to the right.
SSL Configuration
The SSL Configuration screen displays all currently configured SSL ports.
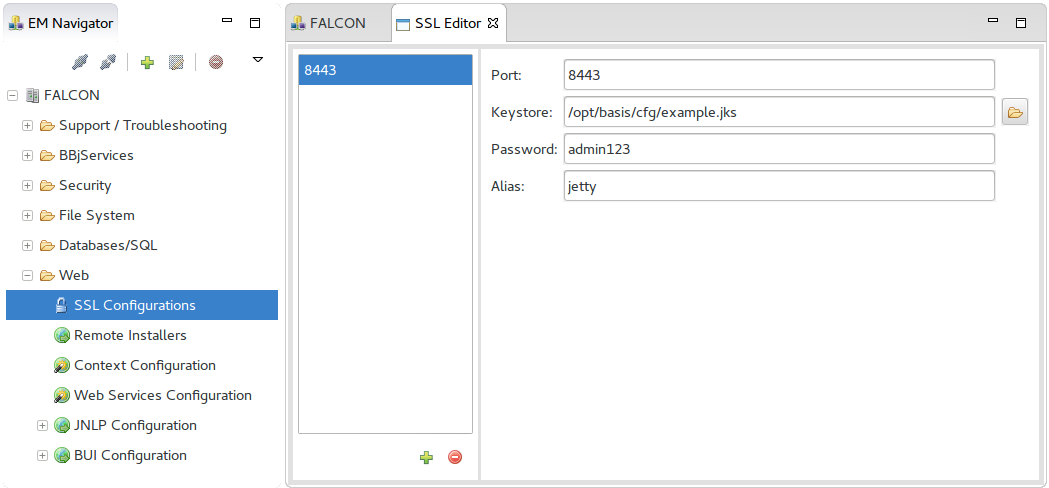
Clicking the icons below the port list allows the administrator to add or delete a SSL Configuration:
![]() Adds a new SSL Configuration.
Adds a new SSL Configuration.
![]() Delete the selected SSL Configuration.
Delete the selected SSL Configuration.
The
SSL Port configuration requires the following information which can be
obtained from your keystore provider.
|
Port |
The HTTP Port number. |
|
Keystore |
Location of the keystore. |
|
Password |
Password for the keystore. |
|
Alias |
The Alias within the keystore. |
The SSL port binding happens at the transport layer in the HTTPS protocol and there is no need to specify which context a port belongs as the transport-layer will validate the incoming packets before handing them for processing.
Advanced SSL Configuration
The integrated Jetty server has disabled protocols SSLv3, TLSv1 and SSLv2Hello because they present security risks. If you want to disable any additional protocol or cipher then this can be done by editing jetty.xml.
Locate the ssl-config entry and embed within exclude-protocol and exclude-cipher elements. Here is an example:
<ssl-config alias="jetty"
keystore="/opt/basis/cfg/example.jks"
keystore-password-enc="B1NhCfk1XmL0/u1WA8aoKQ=="
port="8443">
<exclude-cipher>TLS_DHE_RSA_WITH_AES_128_CBC_SHA</exclude-cipher>
<exclude-protocol>TLSv1.1</exclude-protocol>
</ssl-config>About the Keystore
SSL configuration requires a keystore. The example .jks keystore is supplied with every BBj install and is a great reference for building custom keystores. BBj requires at least two passwords for the keystore and another for the specific certificate used by Jetty. Examine the example.jks using the keytool command provided with Java.
keytool -v -list -keystore example.jks
Keytool creates new keystores as well. Generate a fresh key pair with this command:
keytool -keystore mykeystore.jks -alias jetty -genkey -keyalg RSA
Then, generate a certificate request with this command:
keytool -certreq -alias jetty -keystore mykeystore.jks -file jetty.csr
Send the certificate request to an SSL provider, and they will send back a public key guaranteeing your authenticity. The next step is to import the provider’s response, with this command:
keytool -keystore keystore -import -alias jetty -file response.crt
Finally, configure the keystore and passwords as appropriate in Enterprise Manager.