Enterprise Manager: Remote Database Security
Introduction
The unique structure of BBj provides excellent flexibility when it comes to deployment options. Many BBj applications access data files directly using READ/WRITE as well as via SQL. In addition, many end users require the additional capability of accessing BBj data via 3rd party applications using the BBj ODBC and/or JDBC driver. While this flexibility opens up a world of possibilities, it also presents some security and/or data integrity concerns. For example, what if you want to (1) provide write access to the tables in a database to all users within your application, (2) allow them to access the data remotely via ODBC for reporting purposes, (3) do not want them to be able to update the data outside the application’s framework? BBj 16.00 provides Remote Database Security exactly for this purpose.
In BBj 16.0 and Higher, Configuring Remote Security Using the Enterprise Manager
Open the Remote Security tab on the database editor under YourServer->Databases->YourDatabase:
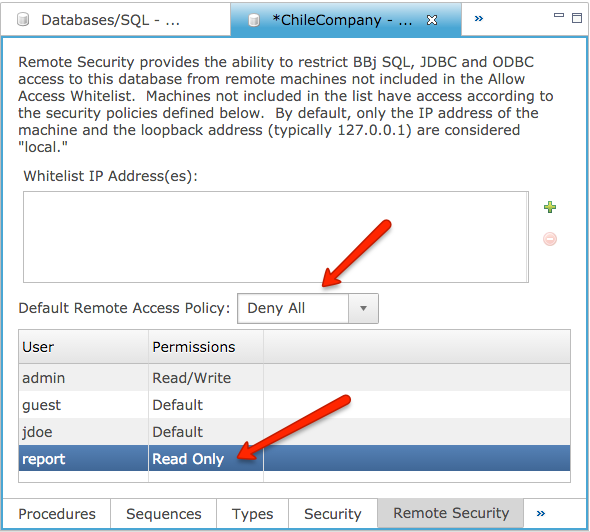
Whitelist IP Address(es)
The whitelist contains a list of any IP addresses to consider “local.” By local we mean that they will not adhere to the remote access policies set in the section below, but rather, treated as if they were the local machine. By default, only the IP address of the machine running BBjServices and the loopback address (typically 127.0.0.1) are considered “local.”
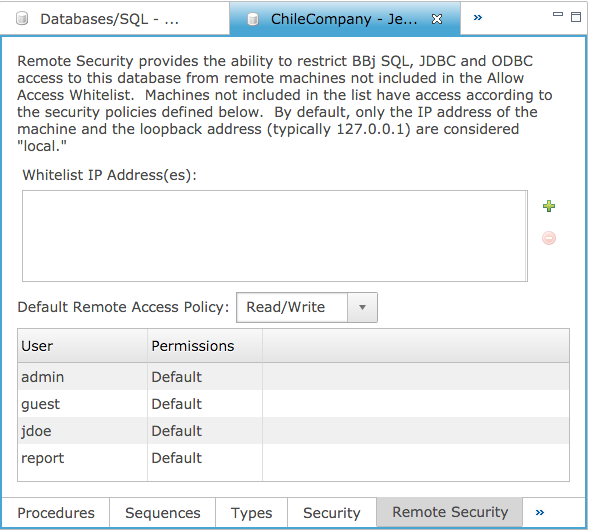
Default Remote Access Policy and User Permissions
This setting works exactly as the standard database access policy setting works under Security. Select the minimum level of access that all users have when connecting from a remote machine. For example, to reject all remote SQL connections, set the default policy to “Deny All” and leave all users set to “Default” (see image below). To grant access to only select users, change their individual permissions to “Read Only” or “Read/Write” as appropriate.